Introduction
In the process of developing software applications, each project necessitates the creation of a mechanism for granting the correct users access (i.e., authentication) and defining their permissions (i.e., authorization). This combination of functionalities is referred to as an “Auth system.”
When deciding between a third-party solution and building an authentication system in-house, there are many important factors you need to consider. There are pros and cons of both approaches. You must determine which of these two choices aligns better with your application requirements.
In this article, I will demonstrate the pros and cons of both approaches in detail to help you make the right decision for handling authentication and authorization in your app.
First, let’s understand the key difference between user authentication and authorization.
Authentication vs Authorization
Authentication is the verification of a user’s identity based on their claims. For instance, on a website, users are categorized as Admin or Customer. When a user logs in as an admin, the app checks if they are indeed an admin for successful authentication, and the same process applies to customers.
In essence, authentication confirms a user’s identity as per their assertion. Whereas authorization determines a user’s access rights within the app after they are authenticated. For instance, a customer can view and edit their own details but not those of others. Meanwhile, an admin can access all customer details except passwords, highlighting the importance of defining access limits based on authorization levels.
The Building Blocks of User Authentication
The authentication process has evolved from basic username and password systems to more advanced methods that incorporate multi-factor authentication (MFA), single sign-on (SSO), going passwordless (biometric or otp-based auth), and social identity providers. These advances are essential in the modern age to protect user data and enhance the user experience.
Before we dive into the pros and cons of building our own authentication system versus using a third-party solution, let’s establish a foundational understanding of what user authentication involves:
User Data Management: This includes storing and managing user profiles, credentials (e.g., passwords or tokens), and user attributes (e.g., email addresses, names, roles).
Authentication Mechanisms: Implementing secure methods for verifying the identity of users, such as password-based authentication, social login (e.g., Google or Facebook), password-less authentication, or multi-factor authentication (MFA).
Security: Ensuring data encryption, protection against common attacks (e.g., XSS, CSRF, and SQL injection), and secure storage and exchange of sensitive user information.
Scalability: The ability to handle growing numbers of users and concurrent authentication requests efficiently.
Customization: Tailoring the authentication process and making it flexible to add more authentication mechanisms and information about users to match your application’s unique requirements and user experience.
Compliance: Data compliance identifies the rules and regulations around your data that you must follow, either imposed by the client you work with or the ruling body in your operating region.
Next, Let’s explore the pros and cons of building our own authentication system.
Building Your Own Authentication System
- Pros
Customization: Building your own authentication system allows you complete control over it. You can choose one or more authentication mechanism(s) for your user’s best experience. You can define your own user attributes according to your needs. Overall, You can design the authentication flow to align perfectly with your application’s needs.
Data Control & Compliance: You have full ownership of user data, which can be critical for compliance, privacy, or regulatory reasons.
Cost Control: People generally think using 3rd party solutions is always cheaper, but this is not true. Once your application grows to ~100k+ users, the 3rd party pricing might hurt you. Depending on your application’s scale, building your own system can be more cost-effective in the long run.
- Cons
Complexity: Developing a secure authentication system is complex and time-consuming. It requires a deep understanding of security best practices, including hashing algorithms, token management, user session management and more. It becomes much more complex when we deal with authentication in distributed systems.
Maintenance Burden: Building your own system means you’re responsible for ongoing maintenance, bug fixes, and security updates. This can divert resources and attention from your core application features. The company I work at has a dedicated team of engineers to maintain the auth system.
Security Risks: Building your own system can introduce security risks if not done correctly. Any vulnerabilities could lead to data breaches and compromised user accounts.
Using a 3rd party Authentication Service
To better analyze the pros and cons of a 3rd party Auth system, let’s have a look at the features provided by two popular players, Auth0 and AWSCognito.
AWS Cognito
Amazon Cognito serves as a comprehensive identity platform for web and mobile applications, functioning as a user directory, authentication server, and authorization service. It supports OAuth 2.0 access tokens and AWS credentials, enabling authentication and authorization from various sources, including the built-in user directory, enterprise directories, and consumer identity providers like Google and Facebook.
Amazon Cognito relies on two integral components to function effectively:
User Pool: This component serves as a centralized user directory, managing user registration, authentication, and account recovery. User Pools enable seamless user management and authentication processes within the Amazon Cognito framework.
Identity Pool: The Identity Pool component facilitates secure short-term access to various AWS services to authenticated users or even guest users. It ensures controlled access and permissions, allowing users to interact securely with other AWS resources and services.
Both the User Pool and Identity Pool can function autonomously or collaboratively, offering flexibility in their operational integration.
Next, we will look at the working flow of the User pool, Identity pool, and also the combined use of these two.
- 1.Working Flow of User Pool
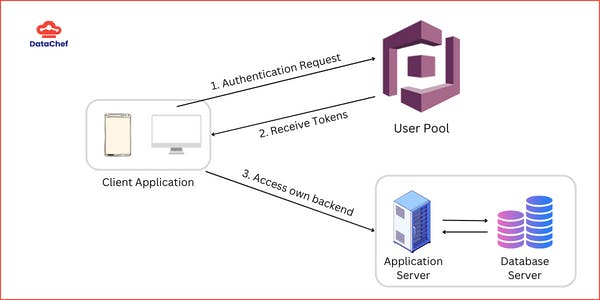
Scenario - 1. Integration with your own backend
Provide user credentials to the Amazon Cognito user pool to get authenticated and receive a token if verified successfully.
Send this token in subsequent requests to access your backend/DB. The backend checks for the token validity with Cognito and grants access to these resources.
Scenario - 2. Integration with AWS Ecosystem
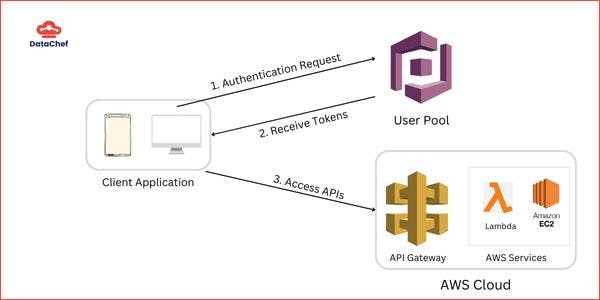
The first step remains the same in this scenario as well. We request the user pool to authenticate the user and send a token back to the requester.
When accessing AWS serverless APIs placed behind an API Gateway, the gateway natively integrates with the user pool to validate the token received in the request; successful validation grants access to resources, while failure results in an immediate request denial.
- 2.Working Flow of Identity Pool
The identity pool grants short-term access to AWS services based on the role matched via Token Attributes or defined IAM Policies.
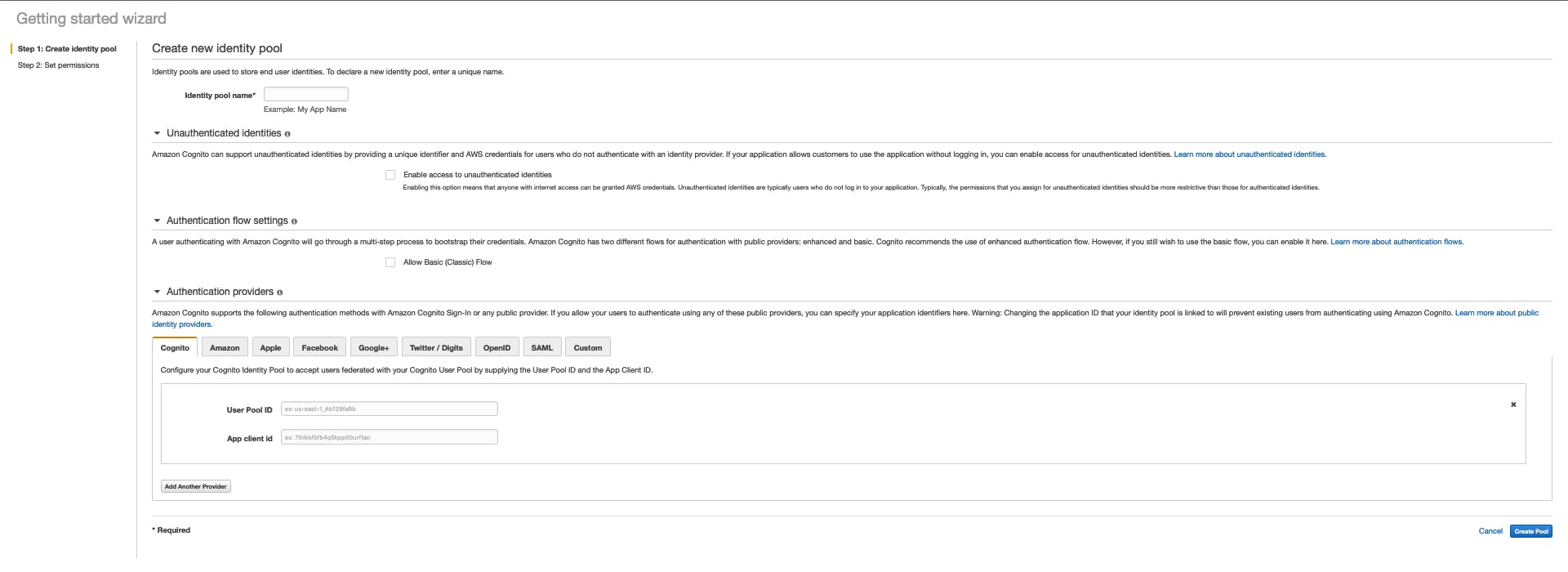
While creating the identity pool, we can configure identity providers like a user pool, any of the social logins, or a custom provider.
We can also configure whether unauthenticated ( guest ) users are allowed to have restrictive access to AWS services.
Upon the completion of authentication by identity providers, they communicate with the Identity Pool by issuing a specific token. Upon token reception, the Identity Pool proceeds to authorize users to varying levels of access.
To implement different access levels, the Identity Pool leverages IAM Roles, offering a structured approach to access management.
Utilizing AWS Security Token Service (STS), the Identity Pool furnishes users with credentials to securely access AWS resources. Below is the AWS Console to create and configure the identity pool.
- 3.Working Flow of User Pool and Identity Pool together
These both work seamlessly together. We have discussed all those points above. It is just that we need to configure User Pool as the identity provider for Identity Pool to make them work together.
AWS Cognito Features
User Pool Creation: Developers create a User Pool in AWS Cognito, which serves as a user directory for the application.
User Registration and Authentication: Users can register and log in using email/password, social identity providers, or federated identities (such as Google or Facebook). AWS Cognito handles the authentication process, including MFA if configured.
Identity Federation: AWS Cognito supports identity federation, allowing users to sign in through external identity providers like SAML or OpenID Connect.
User Profile Management: Developers can store user attributes in Cognito User Pools and customize the schema to include additional data.
Authorization and Access Control: AWS Cognito provides basic access control through groups and roles. Developers can define custom authorization logic within their applications.
User Migrations: It offers tools for migrating users from existing systems to Cognito User Pools.
Security and Compliance: AWS Cognito includes security features like adaptive authentication and encryption. It helps meet compliance requirements, including GDPR and HIPAA.
Integration with AWS Services: Cognito integrates seamlessly with other AWS services, allowing developers to grant fine-grained permissions for accessing AWS resources.
Key Points for AWS Cognito:
Managed service by AWS for user identity and authentication. Identity federation for integrating with external identity providers. Basic access control and user profile management. Seamless integration with other AWS services. Strong security features and compliance support.
2.Auth0
Auth0 is an Identity-as-a-Service (IDaaS) platform that provides authentication and authorization services. It is designed to make it easy for developers to add secure authentication and authorization to their applications. Don’t confuse Auth0 with OAuth. Auth0 is a company that provides auth services whereas OAuth(Open Authorization) is an open protocol that allows secure authorization in a standard way.
Auth0 Features
Auth0 is an Identity-as-a-Service (IDaaS) platform that provides authentication and authorization services. It is designed to make it easy for developers to add secure authentication and authorization to their applications. Here’s the working flow and key points for Auth0:
User Registration and Authentication: Developers integrate Auth0 into their application by adding the Auth0 SDK or configuring it through the Auth0 Dashboard. Users can register and log in using various identity providers such as social media accounts, enterprise SSO, or traditional username/password combinations. Auth0 handles the authentication process, including multi-factor authentication (MFA) if configured.
Identity Providers: Auth0 supports a wide range of identity providers out of the box, including Google, Facebook, Microsoft Azure AD, and more. Developers can also configure custom identity providers if needed.
Authorization and Access Control: Auth0 provides role-based access control (RBAC) and fine-grained authorization policies. Developers can define rules to restrict or grant access based on user attributes, roles, and permissions.
Single Sign-On (SSO): Auth0 enables SSO across multiple applications, allowing users to log in once and access multiple services without re-entering their credentials.
User Profile Management: Auth0 offers features for managing user profiles and attributes. Developers can customize the user profile schema to store additional information.
Customization: Auth0 allows customization of the login page and email templates to match the application’s branding and user experience.
Security and Compliance: Auth0 provides security features like threat detection, anomaly detection, and password policies. It helps developers meet compliance requirements like GDPR and HIPAA.
Analytics and Monitoring: Auth0 provides detailed analytics and logs for monitoring user activity and system performance.
- Key Points for Auth0:
Easy integration with various identity providers.
Robust authentication and authorization capabilities.
Customization options for branding and user experience.
Built-in security and compliance features.
Support for SSO across multiple applications.
Comprehensive analytics and monitoring.
Differences Between Auth0 and AWS Cognito:
Managed Service Provider: Auth0 is a standalone Identity-as-a-Service (IDaaS) platform, while AWS Cognito is an AWS-managed service.
Identity Provider Support: Auth0 offers a wide range of built-in identity providers, whereas AWS Cognito primarily focuses on integrating with AWS services and provides basic identity federation capabilities.
Customization: Auth0 offers extensive customization options for branding and user experience, whereas AWS Cognito provides more limited customization.
Integration: AWS Cognito seamlessly integrates with other AWS services, making it a preferred choice for AWS-centric applications, while Auth0 is agnostic to cloud providers.
Pricing Model: Auth0 typically follows a pay-per-user pricing model, while AWS Cognito pricing depends on factors like active users and data storage. With all comparisons, Cognito is much cheaper and fits with the AWS stack decently well.
Use Cases: Auth0 is well-suited for applications where identity management and authentication are the primary focus. AWS Cognito is a good fit for AWS-centric applications that require basic identity management and want to leverage other AWS services.
Ultimately, the choice between Auth0 and AWS Cognito depends on the specific needs and preferences of the application and the development environment.
So far, we have discussed the features provided by two popular auth providers and we have also compared them. Now, we are better positioned to discuss the pros and cons of 3rd party auth services over a self-developed authentication solution.
- Pros
Rapid Development: Third-party authentication services offer pre-built solutions that can be integrated quickly, accelerating your development timeline. Comes with out-of-the-box support for multiple auth mechanisms, from having old school methods like username-password auth to the newest methods like passwordless auth.
Security Expertise: These service providers invest heavily in hiring security experts to design and develop the auth system, reducing the likelihood of security vulnerabilities and ensuring best practices are followed. These services are battle-tested against common security risks and provide features like MFA, fraud detection, and threat analysis to protect user accounts.
Scalability: Third-party services are typically built to scale effortlessly, handling user authentication for even the largest applications.
Global Reach: Many providers offer worldwide server distribution, ensuring low-latency access for users across the globe.
- Cons
Limited Customization: While configurable, third-party solutions may not perfectly align with your specific needs, leading to compromises in functionality or user experience.
Cost: Depending on your user base and usage, third-party services can become expensive over time, as you pay based on the number of users or authentication requests.
Data Control: You’ll need to trust the third-party provider with user data, which may not be suitable for applications with strict data privacy requirements.
Vendor Dependency: Relying on a third-party service introduces a dependency on its availability and reliability, which may impact your application’s uptime. Vendor lock-in is another problem where it gets very challenging to migrate to another solution if needed.
So far, we have learned the following things: The purpose of having an auth system. The pros and cons of 3rd party authentication services. The pros and cons of building our own authentication system.
Let’s use this knowledge in deciding the auth approach that best suits your project and client/organization.
Making the Decision
The decision to build your own authentication system or use a third-party service hinges on various factors:
Project Scope: Consider the complexity of your application and the resources available. Smaller projects with limited resources may benefit from third-party solutions, while larger, more complex applications may require a custom approach.
Development Resources: In-House Expertise: Assess your development team’s expertise in authentication and security. Building your system requires a deep understanding of security best practices.
Availability of Time and Talent: Evaluate whether you have the time and talent to build and maintain a custom solution without sacrificing other critical development tasks. If you have a small development team (<20-30), it’s more suitable for you to use a 3rd party solution keeping compliance issues into consideration.
Customization Needs: Evaluate the degree of customization required for your authentication process. If your application demands a highly tailored experience, building your own system may be the better choice.
Security Requirements: If your application handles sensitive data or must comply with specific security standards, a third-party service with a strong security track record can be a safer bet.
Long-Term Perspective: Think about the long-term maintenance and scalability of your authentication system. Building your own requires ongoing commitment, while third-party services can offload much of that responsibility.
Time-to-Market: Consider your application’s time-to-market requirements. Sometimes we get considerably less time to build and launch a product to compete in the market. In such cases, third-party solutions offer faster integration but may have limitations.
Budget Constraints: Consider your budget constraints and how the pricing models of third-party services align with your financial resources.
Data Compliance: See if the 3rd party service you choose complies with the regulatory requirements of your user’s data. Otherwise, you would need to build your own auth. When working with banking clients, many times we need to deploy applications on-premise due to compliance issues, and this is where most of the 3rd party services are ruled out.
These are the eight pointers you should remember while deciding the authentication system you should use for your application.
Conclusion
User authentication is a critical aspect of modern application development, and deciding to build your own system or use a third-party solution is not to be taken lightly. Both options have their merits and drawbacks, and the choice ultimately depends on your project’s unique requirements, resources, and priorities.
Building your authentication system can provide complete control and cost savings if you have the in-house expertise, time, and customization needs. On the other hand, leveraging third-party solutions offers rapid implementation, security features, and scalability, making them a pragmatic choice for many projects.
In either case, prioritize security, user experience, and regulatory compliance. Whichever path you choose, it’s essential to stay informed about evolving authentication standards and best practices to ensure your application’s ongoing security and success.

